Intro
This alert highlights the exploitation of CVE-2024049138, a Windows privilege escalation vulnerability.
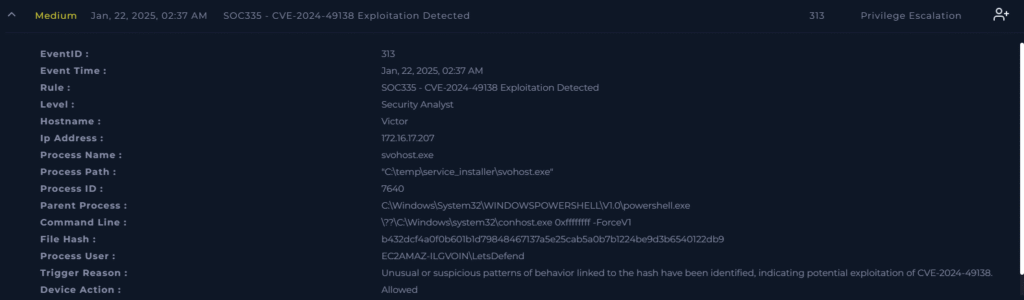
Alert Details
| Field | Value |
| EventID | 313 |
| Event Time | Jan 22, 2025, 02:37 AM |
| Rule | SOC335 – CVE-2024-49138 Exploitation Detected |
| Level | Security Analyst |
| Hostname | Victor |
| IP Address | 172.16.17.207 |
| Process Name | svohost.exe |
| Process Path | “C:\temp\service_installer\svohost.exe” |
| Process ID | 7640 |
| Parent Process | C:\Windows\System32\WINDOWSPOWERSHELL\V1.0\powershell.exe |
| Command Line | ??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 |
| File Hash | b432dcf4a0f0b601b1d79848467137a5e25cab5a0b7b1224be9d3b6540122db9 |
| Process User | EC2AMAZ-ILGVOIN\LetsDefend |
| Trigger Reason | Unusual or suspicious patterns of behavior linked to the hash have been identified, indicating potential exploitation of CVE-2024-49138. |
| Device Action | Allowed |
What is svchost.exe?
svchost.exe is a system process in Windows that hosts and manages various Windows services. Its functions is to group related services together within a single process, which helps conserve system resources. Cybercriminals frequently exploit this service by naming malicious files and processes something similar like svohost.exe.
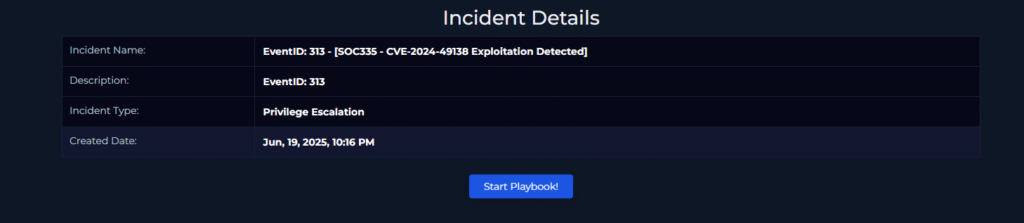
After taking ownership of the alert and assigning it to ourselves we can start the playbook!
For play 1 we need to select the Threat Indicator.
I selected “Unknown or unexpected outgoing internet traffic”.
For play 2 we need to check if the malware is quarantined/cleaned.
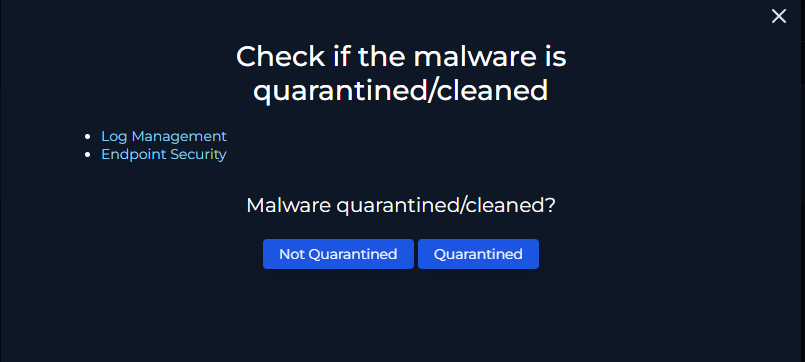
We can check Log Management and Endpoint Security.
First lets look at our Log Management. Lets use the IP address of 172.16.17.207 from the alert in our search.
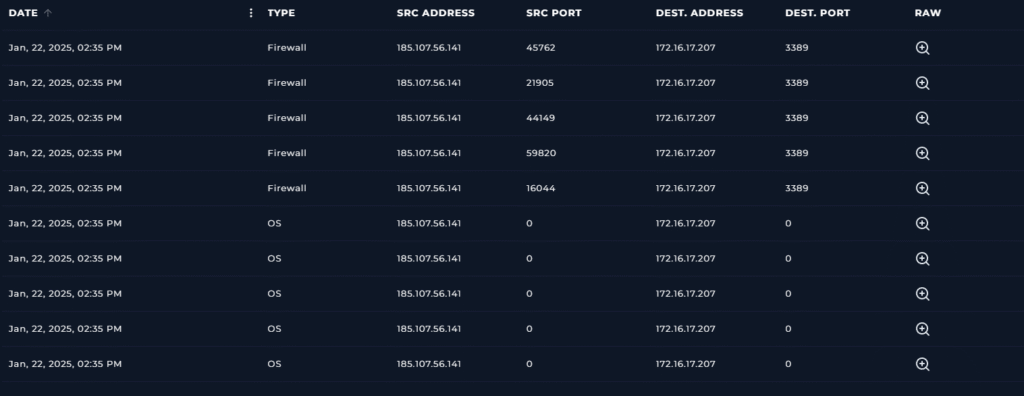
We know the alert was generated at Jan 22, 2025, 02:37 AM so lets look for any indicators for around that time.
All logs with the filter show a date and time of Jan, 22, 2025, 02:35 PM. I notice that an IP address of 185.107.56.141, which is a public IP outside of our network, is connecting or attempting to connect to our endpoint through 3389. Which is a port used for RDP, remote desktop protocol.
Lets look into the log details.
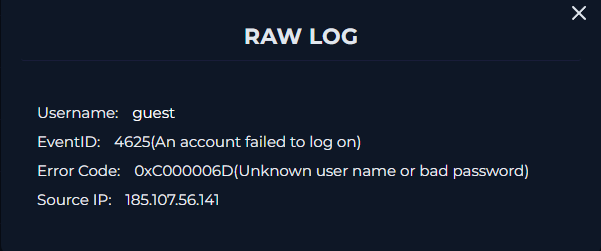
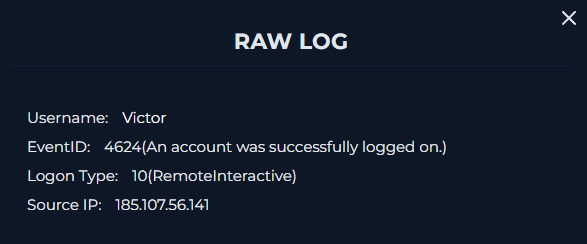
We see an unsuccessful logon with from guest and then a successful logon from Victor.
We also see that the logon type was 10, which indicates a user logged onto a computer remotely using Terminal Services, Remote Desktop, or Remote Assistance.
Lets now go look at the endpoint logs from Victors machine.
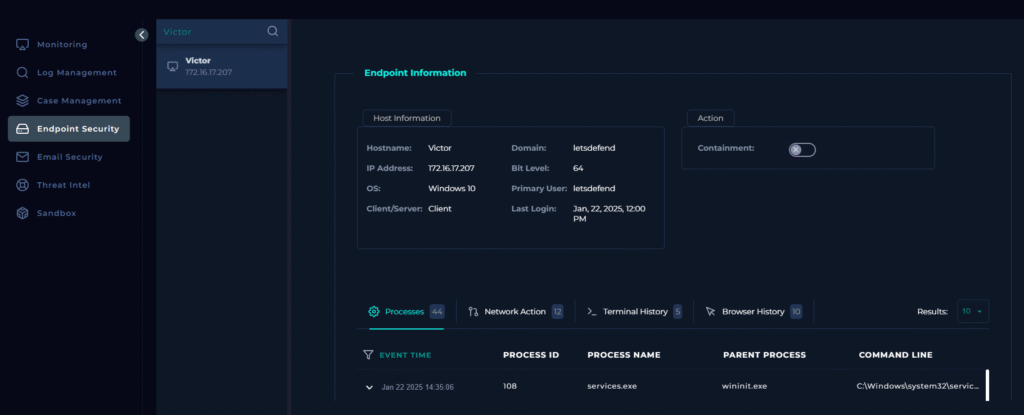
We have different logs we can analyze, Processes, Network Action, Terminal History, Browser History. I know that the process in the alert was svohost.exe so I will start by looking at the Processes tab. Based off the alert I have good idea of what I should be looking for, which is a PowerShell running from svohost.exe.
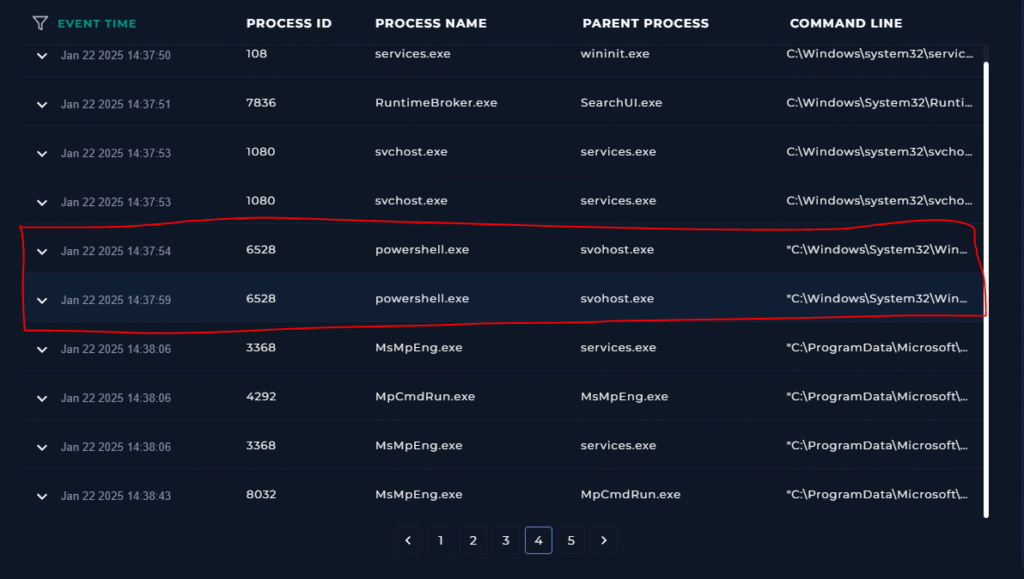
I found two events that raise suspicion.
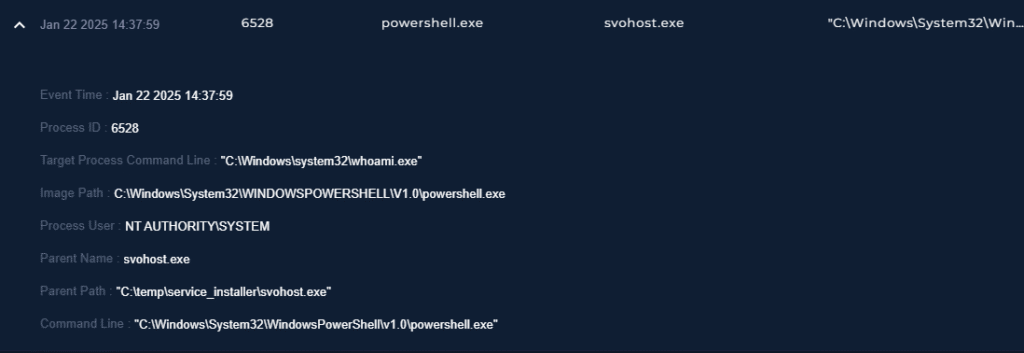
Analyzing the event details shows good information:
- Process User is NT AUTHORITY\SYSTEM which has the highest level of permissions.
- Parent Process is svohost.exe which mimics svchost.exe
- svohost.exe lives in the temp directory which is suspicious
- svohost.exe launched PowerShell and ran the whoami command which allows attackers to quickly see if privilege’s have been escalated
We can also check the terminal history.
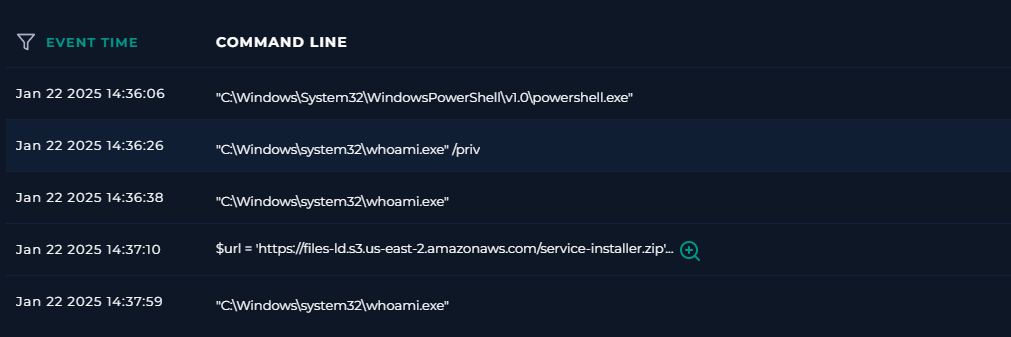
Based off the logs here it looks like the attacker checks who they are and what privileges they have before downloading the malware. Then after they download the malware they check again to confirm their privilege escalation.
This gives me enough confidence to say the malware is not quarantined/cleaned.
For play 3 we need to analyze the malware using 3rd party tools and assess if it malicious or not.
We have the file hash from the alert. We can navigate to VirusTotal to gather information about the malware.
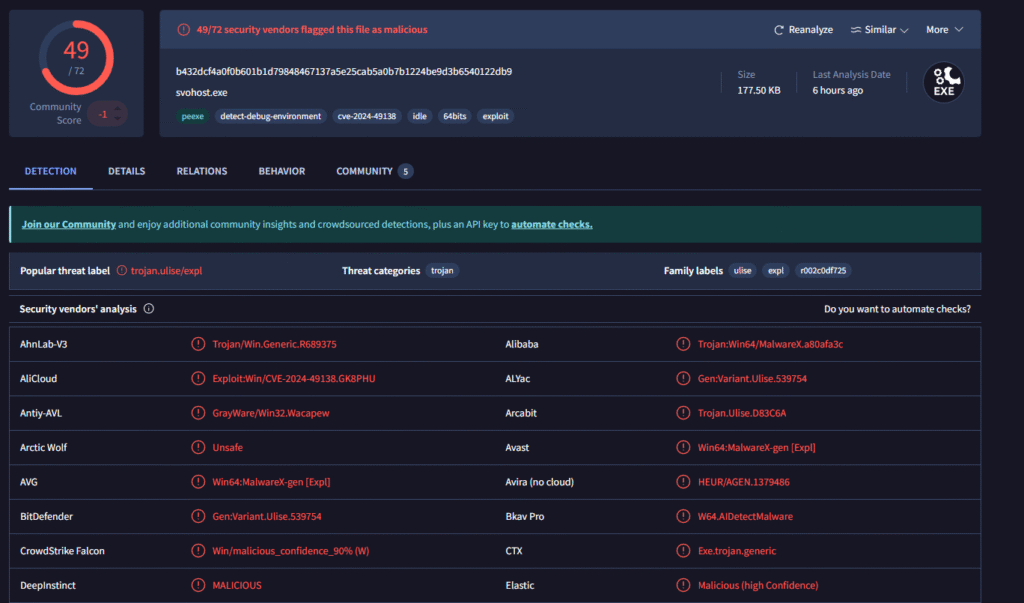
Based off the VirusTotal report we know this is malicious.
For play 4 we need to check is someone made a request to the C2 server.
We analyzed this earlier when we saw an unknown IP (C2) attempting and successfully logging into our victim machine via RDP on port 3389.
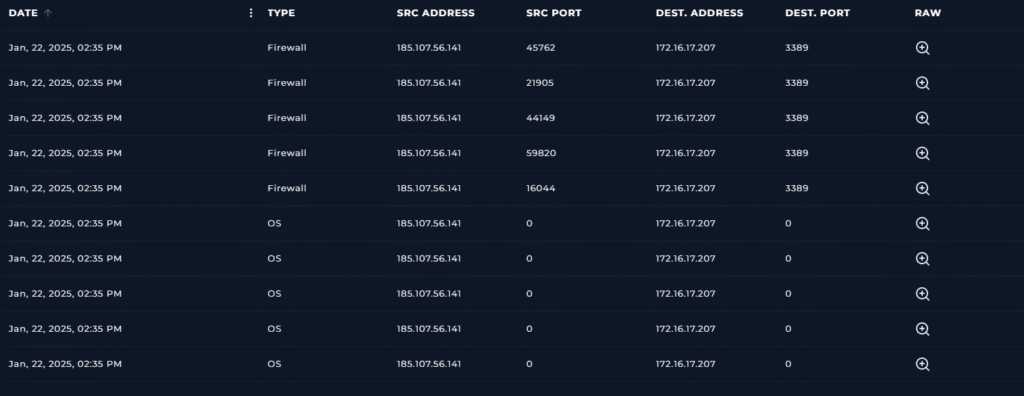
So the answer is Accessed.
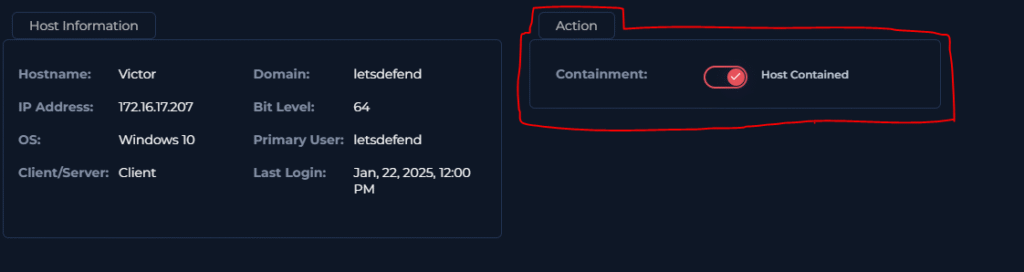
For play 5 we need to contain the device!
We can navigate to Victor’s device in the Endpoint Security tab and turn on containment.
Next we can add artifacts before closing out the alert.
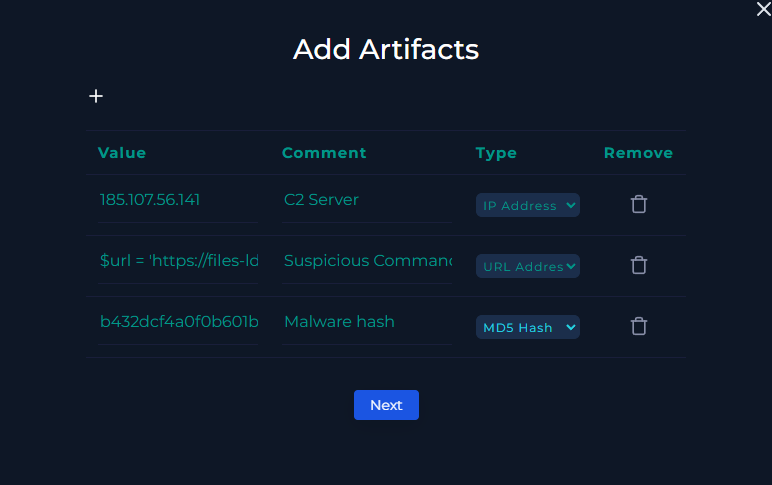
I added the C2 Server, Malware hash, and suspicious URL command.
Analyst Notes:
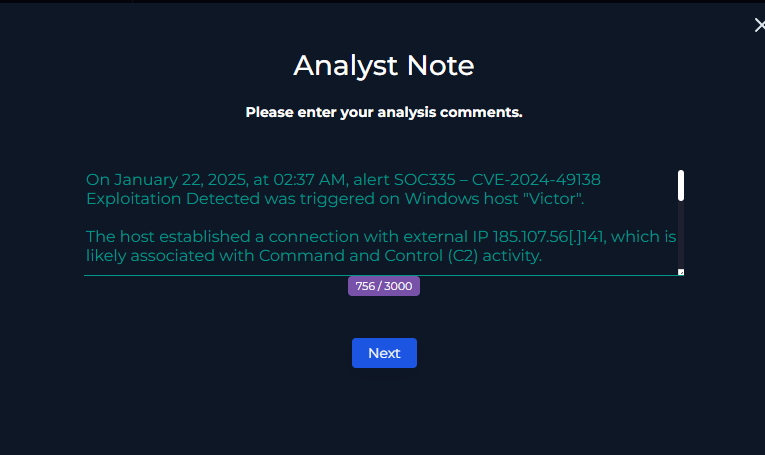
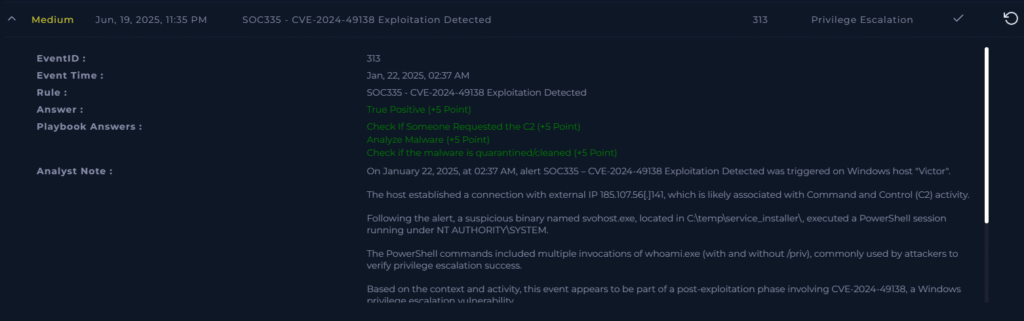
And close the alert!
Thanks for reading!
Leave a Reply